Tesco Impersonation Attacks Target Citizens In Cost Of Living Crisis
Since September 8, 2022, we have seen an increase in email phishing attacks impersonating British supermarket chain Tesco. These attacks are sent via legitimate email marketing tool MailChimp using compromised addresses, display name impersonation, and stylized HTML templates. Together with subject lines and email copy that takes advantage of the UK’s cost of living crisis, these phishing emails socially engineer the victim to click on a phishing link and entering their credentials on a phishing website.
Quick summary of these attacks
- Vector and type: Email phishing
- Techniques: Brand impersonation and business email compromise
- Payload: Phishing link to harvest credentials
- Targets: Organizations in North America and the UK
- Platform: Outlook 365
- Bypassed secure email gateway: Yes
The attack has been designed to bypass traditional email security, including secure email gateways (SEGs) to ensure delivery to victims’ mailboxes. It achieves this through a variety of techniques, including:
- Using a compromised email domain for the sender address
- Being sent via legitimate email marketing tool Mailchimp
- Having perfect configuration of email authentication (SPF, DKIM, and DMARC).
- Using invisible Unicode characters to help bypass linguistic detection
The emails offer the recipient to enter an online competition to win vouchers towards their grocery shopping.
What the attacks look like
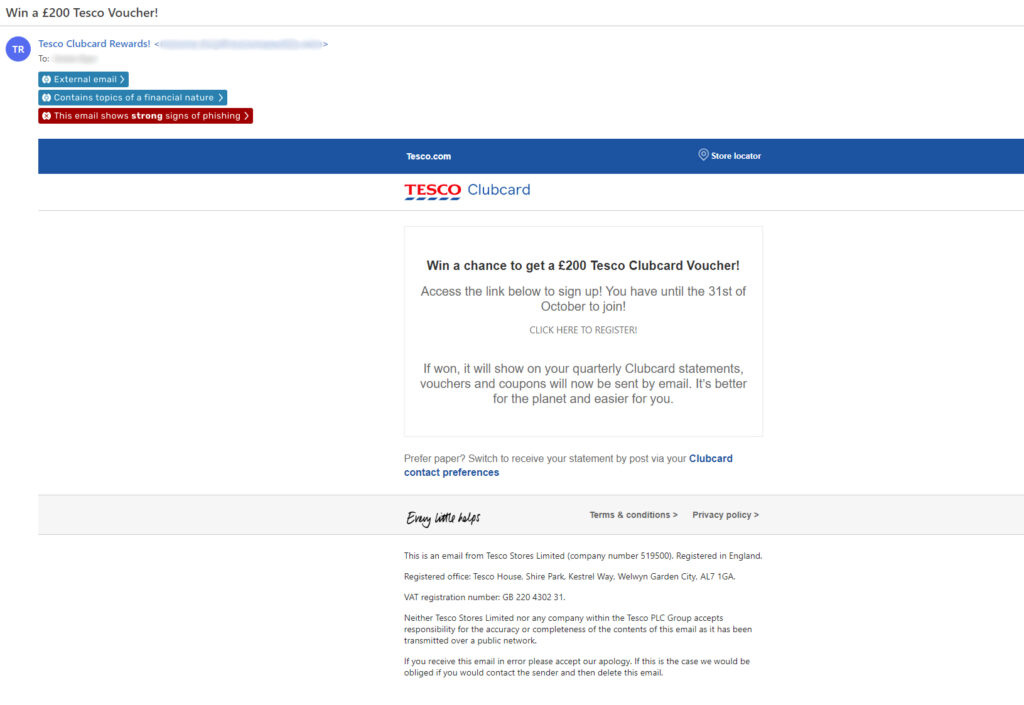
Below is a screenshot of one of these emails. You can see the display name impersonation (‘Tesco Clubcard Rewards!’), which is used to hide the compromised address the attack is sent from.
The email also contains a high-resolution Tesco Clubcard logo and legitimate email footer.
Vulnerable UK Consumers Targeted by Grocery Phishing Scam; Is the US Next?
Screenshot of Tesco brand impersonation phishing email, with Egress Defend banners anti-phishing alert visible
The emails also use invisible Unicode characters within the HTML to avoid detection by SEGs. These characters break up key words that are commonly detected by traditional linguistic analysis, such as ‘£’, ‘voucher’, and ‘won’.
Screenshot showing invisible Unicode character embedded within the phishing email
Egress analysis
These phishing emails have been designed to take advantage of the UK’s current cost of living crisis. While we’ve seen this phishing attack targeting organizations in both North America and the UK, the volume is three times higher in the UK, likely driven by Tesco’s household status in the country.
Increases in food prices, and other essential bills, caused by inflation dominate the daily headlines. As a result, cybercriminals are doubling down on phishing emails that socially engineer their victims with fraudulent competitions and other schemes that offer ways for people to reduce their spending at a time when they’re most receptive to this messaging.
Avoiding detection
This Tesco phishing scam is particularly convincing. Firstly, the attacker has taken multiple steps to ensure delivery. By sending via a legitimate email marketing tool, MailChimp, the attacker leverages the address’ existing domain authority to ensure delivery. The attack also uses hidden Unicode characters, an advanced evasion technique that enabled it to bypass traditional email security that failed to detect it. . As part of the HTML template used, there are also legitimate Tesco hyperlinks to their terms and conditions and privacy policy. These legitimate links also help the phishing attack to avoid detection.
Brand impersonation
Once the phishing attack is in the recipient’s mailbox, the attacker then uses display name and highly stylized brand impersonation to convince the victim of its legitimacy. This includes the overall HTML template using the Tesco logo, slogan (‘Every little helps’), brand colors, and email footer.) As mentioned, the subject line (‘Win a £200 Tesco Voucher’) and its contents are used to further socially engineer the victim by offering them help with their shopping bills.
Phishing website
When the unsuspecting recipient clicks the phishing link, they are taken to a website that harvests their credentials by asking them to log into or create an account to enter the competition. These stolen credentials can then be used by the original cybercriminal in breach replay attacks (where the credentials are used to access and compromise other accounts) or be sold to other cybercriminals. At the time of detection by the Egress team, the phishing links were bypassing detection by SEGs and weren’t recorded on a blocklist. It’s typical for these phishing websites to be live for a short period of time until they are detected, at which point the cybercriminal will use a new URL.
Setting up future scams
Finally, the email body copy shows evidence of the attacker laying the groundwork for future phishing attacks re-targeting their victims, with: ‘…vouchers and coupons will now be sent by email.’ It is possible that a future attack will tell victims they have been awarded a voucher, with a likely payload of another phishing link to a website asking for their credentials or even a malicious attachment. There is evidence from previous phishing attacks that people who fall victim once are re-targeted by the same cybercriminals as they are identified as ‘easy’ targets.
The takeaways
Organizations need to be aware how attackers leverage the 24-hour news cycle to generate new, targeted attacks. Regulatory bodies and government agencies routinely highlight these trends, and organizations can proactively include them in their security awareness messaging.
Organizations also need to ensure they have anti-phishing technology to detect advanced phishing attacks directly within people’s inboxes, so recipients are alerted to attacks that are specifically engineered to evade detection by SEGs.
Individuals also need to be aware of common phishing techniques, such as competitions and giveaways. It is usually possible to verify the legitimacy of such schemes through a company’s website or social media profiles, or by getting in touch directly.
Source: Egress